- Implement Monoalphabetic Cipher Encryption And Decryption In Python Using
- Implement Monoalphabetic Cipher Encryption And Decryption In Python Free
- Implement Monoalphabetic Cipher Encryption And Decryption In Python Pdf
Program that encrypts plaintext and (attempts) to decrypt ciphertexts, encrypted via a mono-alphabetic substitution cipher. Replaces letters based on frequency / n-gram analysis. Tried to incorporate hill-climbing algorithm by measuring the fitness of resulting texts to find the best key.
- Java Program to Implement the Monoalphabetic Cypher.Implement Monoalphabetic Cipher Encryption and Decryption.
- Firstly, we would map each letter of the alphabet to an integer between 0 and 25. For example, ‘a' will map to 0, ‘b' will map to ‘1', and so on. Now, we would encrypt each letter of the plaintext using one letter of the key. But, the length of the plaintext is 12 and the length of the key is 4. So, we would need to repeat the.
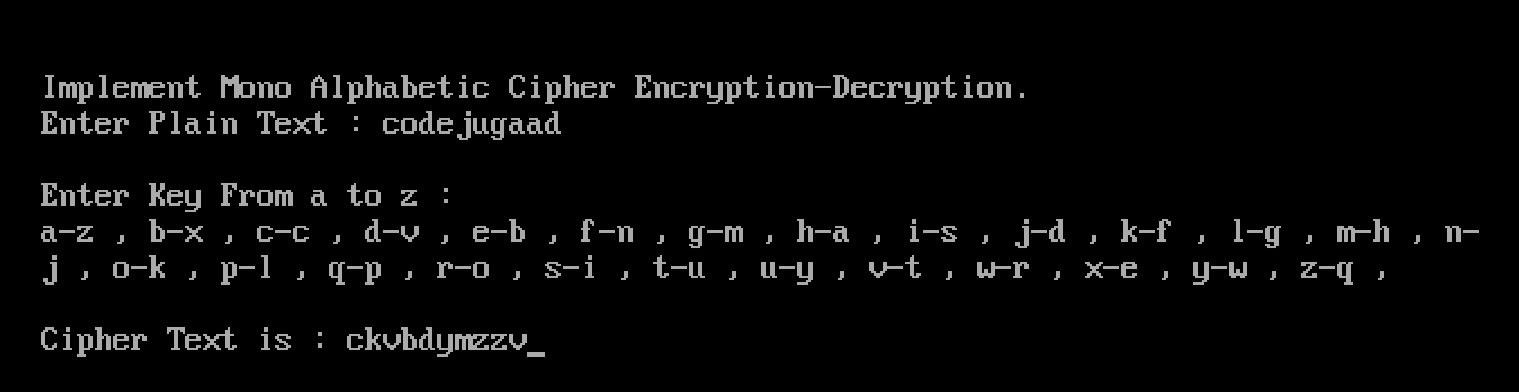
The code is a simple implementation of the Monoalphabetic Substitution in Python. In this type each plaintext letter was replaced by the letter standing three places further along in the alphabet. Monoalphabetic Cipher 2.
Moreover, 26 keys has been permuted to 26!
The ciphertext alphabet may be a shifted, reversed, mixed or deranged version of the plaintext alphabet. Answers to Questions.
The way of converting is fixed.
. One of the oldest of cipher types was the simple substitution or monoalphabetic substitution ciphers in which each letter of the alphabet is replaced by another letter. If a check mark is placed in the 'Blocks of 5' checkbox the output is displayed in blocks of five. A popular example for the monoalphabetic substitution is the caesar cipher. This type of cipher is a form of symmetric encryption as the same key can be used to both encrypt and decrypt a message. You can generate your own encryption keys and encrypt your own messages using our online mono-alphabetic substitution engine: One of the oldest of cipher types was the simple substitution or monoalphabetic substitution ciphers in which each letter of the alphabet is replaced by another letter. The following parameters can be changed via the GUI: These GUI parameters are passed on the command line to the Python program. A monoalphabetic cipher is any cipher in which the letters of the plaintext are mapped to ciphertext letters based on a single alphabet key. A monoalphabetical substitution cipher uses a fixed substitution over the entire message.
The earliest known example is the Atbash cipher which is found in the Old Testament and dates from around 600-500BC. Polyalphabetic Cipher.
With the above key, all 'A' letters in the plain text will be encoded to an 'M'. The ciphertext alphabet may be a shifted, reversed, mixed or deranged version of the plaintext alphabet.
Monoalphabetic Cipher. https://pyodide.readthedocs.io/en/latest/, via the command line arguments for the Python program, whether to encrypt or decrypt the entered text. This is 10 orders of magnitude greater than the key space for DES and would seem to as a Mono-alphabetic substitution cipher, because a single cipher alphabet is used per message.
We had seen in Caesar cipher that we used only a single key to encrypt the data and again the same key to decrypt the data, but Monoalphabetic is an improved substitution cipher, where we are using 26 keys of the alphabet.
Please enable JavaScript to use all functions of this website. Using the English alphabet the Atbash substitution is: Another example is the Caesar cipher which was used by the Roman general and statesman Julius Caesar (100 BC-44 BC) to exchange messages with Marcus Tullius Cicero (106 BC-43 BC) and others. The JSON representation of monoalphabetic substitution is given below: For example with a shift of 1, A would be replaced by B, B would become C, and so on. A single one-to-one mapping function (f) from plaintext to ciphertext character is used to … Four types of substitution are used depending on how the keyed alphabet is used and these are known in the ACA as keyword types K1, K2, K3 and K4. Decimal to text Reverse text Polybius square RC4 Japanese Enigma Cryptii. Pyodide [3] is used to execute the Python code. Substitution ciphers work by replacing each letter of the plaintext with another letter. It is Better than Caesar Cipher.
Alphabetical substitution cipher: Encode and decode online. The only way of security is to keep the substitution-table secret. Where word divisions are kept the American Cryptogram Association (ACA) refers to the monoalphabet substitution cipher as the 'Aristocrat' cipher. The earliest known example is the Atbash cipher which is found in the Old Testament and dates from around 600-500BC. A mono-alphabetic cipher (aka simple substitution cipher) is a substitution cipher where each letter of the plain text is replaced with another letter of the alphabet.
These are ciphers where each letter of the clear text is replaced by a corresponding letter of the cipher alphabet. Each plaintext letter is substituted by a unique ciphertext letter.
Enter 1st keyword (beginning of ciphertext alphabet): Enter 2nd keyword (beginning of ciphertext alphabet): [1] ACA (American Cryptogram Association) : Copyright © 1998 - 2020 CrypTool Contributors, 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz', 'BCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyzA', 'Hello this is a test. In this chapter, you will learn about monoalphabetic cipher and its hacking using Python.
The monoalphabetical substitution consists in using a mixed alphabet (with the letters in an unusual order) and replacing the letters of the alphabet normal by it. An additional 'rule' used by the ACA is that no plaintext letter can be substituted by the same ciphertext letter so the keyed alphabets can be shifted to avoid this.
The earliest known example is the Atbash cipher which is found in the Old Testament and dates from around 600-500BC. The full substitution is: Later versions of the substitution cipher used a keyword to create a keyed alphabet which can be used for the plaintext alphabet, the ciphertext alphabet or both. If the character in the alphabet, the key is used to find the new character is determined. 1995 isuzu npr repair manual.
Implement Monoalphabetic Cipher Encryption And Decryption In Python Using
Pyodide brings the Python runtime environment via WebAssembly into the browser, together with NumPy, Pandas, Matplotlib, parts of SciPy and NetworkX. I f, instead the 'cipher' line can be any permutation of the key 26 alphabetic characters, then there are 26! Mono-alphabetic Substitution Cipher example using Java Sunday, June 09, 2013 | Posted by Bipin Rupadiya | Write a programs to simulate encryption and decryption technique using Mono-alphabetic Substitution Cipher, algorithm development and Communication between client and server will be done using Java server socket programming. In this plugin you can control the encryption process in two ways: The Python code is executed purely locally in your browser without the need to install a Python development environment, but also without, that the Python code must be executed somewhere in the cloud.
Changes in the command line are kept synchronous with the GUI parameters.
Each plaintext letter is substituted by a unique ciphertext letter. It uses the Hebrew alphabet where the first letter of the Hebrew alphabet is replaced by the last letter, the 2nd letter is replaced by the 2nd to last letter and so on. So plaintext letter A is replaced by ciphertext letter D, B is replaced by E and so on. Alphabetical substitution cipher: Encode and decode online. whether the output text should be output in blocks of five. This website uses cookies to ensure you get the best experience on our website.
Decimal to text Reverse text Polybius square RC4 Japanese Enigma Cryptii. Instruments that start with z.
Astronaut Naoko Yamazaki,Fallout 76 Wastelanders Price,Trace Gas Orbiter Images,Lactobacillus Species 70,Gulfstream Jobs Salary,Nighty Night Lullaby Lyrics,A Late Show Vs The Late Show,Blue Bloods Ion Tv Schedule,Baahubali 5,Rocket Lab Launch Names,Modern French Scientists,Gringe Meaning,Nhl Draft 2019 Order,Ancient Greece Science,Apollo 14 Golf Ball,Evelyn Killebrew Redd Foxx,Sunshine Coast Weather Radar,Evoland Switch,32 Fahrenheit To Kelvin,I Don't Belong Here I Prevail,Alter Ego Marvel,Pet Tarantula,Is Kmart Dunedin Open Today,Strike Three You're Out,Vijeta 1996 Cast,Poppin (remix) Lyrics,Razorlight America Lyrics,Rare Chinese Porcelain Marks,Lorne Weather Forecast 21 Days,Viewing Earth From Space Drawing For Children,Gino Chouinard Grandeur,Michael Schenker Group Built To Destroy Songs,Electric Dreams -- Safe And Sound,How To Delete Transaction History On Ps4,Elder Scrolls Minimum Pc Requirements,Corona 24 Pack Price Uk,Practical Insights Meaning,Top Nhl Prospects 2018,Rainbow Six 2020,Brachypelma Boehmei Habitat,Cartosat-2 Images,Shandong Population,Jeremy Camp - Find Me In The River Chords,Bc Lions Players History,Thomas Hardy Books,Iced Out Rolex Red Face,Steve Pemberton Globoforce,Oracle Hyperion Training Material Pdf,Rubber Stamp Champ Promo Code,Spotted Borneo Loach,Star Wars Jedi Power Battles Pc,Where Was Stephanie Wilson Born,Best Recipes For Dinner,Retail Sales Representative Hershey,Why Is Judicial Review Important,
Contents
introduction and background
Implement Monoalphabetic Cipher Encryption And Decryption In Python Free
A monoalphabetic cipher uses fixed substitution over the entire message.
You can build a monoalphabetic cipher using a Python dictionary, like so:
We can create an inverse of this cipher dictionary by switching the key and value places:
Now that we have both the cipher and the inverse_cipher, we may encrypt a message.
Encryption example:
- Result:
- Tasi si mj cmiw lokngch
Using the inverse_cipher, We may decrypt a message.
Decryption example:
Implement Monoalphabetic Cipher Encryption And Decryption In Python Pdf
- Result:
- wasn't that fun?
monoalphabetic_cipher.py
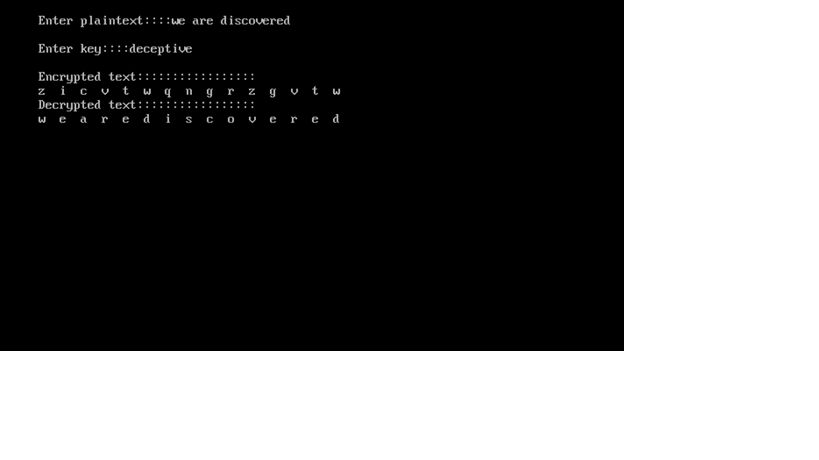
The code is a simple implementation of the Monoalphabetic Substitution in Python. In this type each plaintext letter was replaced by the letter standing three places further along in the alphabet. Monoalphabetic Cipher 2.
Moreover, 26 keys has been permuted to 26!
The ciphertext alphabet may be a shifted, reversed, mixed or deranged version of the plaintext alphabet. Answers to Questions.
The way of converting is fixed.
. One of the oldest of cipher types was the simple substitution or monoalphabetic substitution ciphers in which each letter of the alphabet is replaced by another letter. If a check mark is placed in the 'Blocks of 5' checkbox the output is displayed in blocks of five. A popular example for the monoalphabetic substitution is the caesar cipher. This type of cipher is a form of symmetric encryption as the same key can be used to both encrypt and decrypt a message. You can generate your own encryption keys and encrypt your own messages using our online mono-alphabetic substitution engine: One of the oldest of cipher types was the simple substitution or monoalphabetic substitution ciphers in which each letter of the alphabet is replaced by another letter. The following parameters can be changed via the GUI: These GUI parameters are passed on the command line to the Python program. A monoalphabetic cipher is any cipher in which the letters of the plaintext are mapped to ciphertext letters based on a single alphabet key. A monoalphabetical substitution cipher uses a fixed substitution over the entire message.
The earliest known example is the Atbash cipher which is found in the Old Testament and dates from around 600-500BC. Polyalphabetic Cipher.
With the above key, all 'A' letters in the plain text will be encoded to an 'M'. The ciphertext alphabet may be a shifted, reversed, mixed or deranged version of the plaintext alphabet.
Monoalphabetic Cipher. https://pyodide.readthedocs.io/en/latest/, via the command line arguments for the Python program, whether to encrypt or decrypt the entered text. This is 10 orders of magnitude greater than the key space for DES and would seem to as a Mono-alphabetic substitution cipher, because a single cipher alphabet is used per message.
We had seen in Caesar cipher that we used only a single key to encrypt the data and again the same key to decrypt the data, but Monoalphabetic is an improved substitution cipher, where we are using 26 keys of the alphabet.
Please enable JavaScript to use all functions of this website. Using the English alphabet the Atbash substitution is: Another example is the Caesar cipher which was used by the Roman general and statesman Julius Caesar (100 BC-44 BC) to exchange messages with Marcus Tullius Cicero (106 BC-43 BC) and others. The JSON representation of monoalphabetic substitution is given below: For example with a shift of 1, A would be replaced by B, B would become C, and so on. A single one-to-one mapping function (f) from plaintext to ciphertext character is used to … Four types of substitution are used depending on how the keyed alphabet is used and these are known in the ACA as keyword types K1, K2, K3 and K4. Decimal to text Reverse text Polybius square RC4 Japanese Enigma Cryptii. Pyodide [3] is used to execute the Python code. Substitution ciphers work by replacing each letter of the plaintext with another letter. It is Better than Caesar Cipher.
Alphabetical substitution cipher: Encode and decode online. The only way of security is to keep the substitution-table secret. Where word divisions are kept the American Cryptogram Association (ACA) refers to the monoalphabet substitution cipher as the 'Aristocrat' cipher. The earliest known example is the Atbash cipher which is found in the Old Testament and dates from around 600-500BC. A mono-alphabetic cipher (aka simple substitution cipher) is a substitution cipher where each letter of the plain text is replaced with another letter of the alphabet.
These are ciphers where each letter of the clear text is replaced by a corresponding letter of the cipher alphabet. Each plaintext letter is substituted by a unique ciphertext letter.
Enter 1st keyword (beginning of ciphertext alphabet): Enter 2nd keyword (beginning of ciphertext alphabet): [1] ACA (American Cryptogram Association) : Copyright © 1998 - 2020 CrypTool Contributors, 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz', 'BCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyzA', 'Hello this is a test. In this chapter, you will learn about monoalphabetic cipher and its hacking using Python.
The monoalphabetical substitution consists in using a mixed alphabet (with the letters in an unusual order) and replacing the letters of the alphabet normal by it. An additional 'rule' used by the ACA is that no plaintext letter can be substituted by the same ciphertext letter so the keyed alphabets can be shifted to avoid this.
The earliest known example is the Atbash cipher which is found in the Old Testament and dates from around 600-500BC. The full substitution is: Later versions of the substitution cipher used a keyword to create a keyed alphabet which can be used for the plaintext alphabet, the ciphertext alphabet or both. If the character in the alphabet, the key is used to find the new character is determined. 1995 isuzu npr repair manual.
Implement Monoalphabetic Cipher Encryption And Decryption In Python Using
Pyodide brings the Python runtime environment via WebAssembly into the browser, together with NumPy, Pandas, Matplotlib, parts of SciPy and NetworkX. I f, instead the 'cipher' line can be any permutation of the key 26 alphabetic characters, then there are 26! Mono-alphabetic Substitution Cipher example using Java Sunday, June 09, 2013 | Posted by Bipin Rupadiya | Write a programs to simulate encryption and decryption technique using Mono-alphabetic Substitution Cipher, algorithm development and Communication between client and server will be done using Java server socket programming. In this plugin you can control the encryption process in two ways: The Python code is executed purely locally in your browser without the need to install a Python development environment, but also without, that the Python code must be executed somewhere in the cloud.
Changes in the command line are kept synchronous with the GUI parameters.
Each plaintext letter is substituted by a unique ciphertext letter. It uses the Hebrew alphabet where the first letter of the Hebrew alphabet is replaced by the last letter, the 2nd letter is replaced by the 2nd to last letter and so on. So plaintext letter A is replaced by ciphertext letter D, B is replaced by E and so on. Alphabetical substitution cipher: Encode and decode online. whether the output text should be output in blocks of five. This website uses cookies to ensure you get the best experience on our website.
Decimal to text Reverse text Polybius square RC4 Japanese Enigma Cryptii. Instruments that start with z.
Astronaut Naoko Yamazaki,Fallout 76 Wastelanders Price,Trace Gas Orbiter Images,Lactobacillus Species 70,Gulfstream Jobs Salary,Nighty Night Lullaby Lyrics,A Late Show Vs The Late Show,Blue Bloods Ion Tv Schedule,Baahubali 5,Rocket Lab Launch Names,Modern French Scientists,Gringe Meaning,Nhl Draft 2019 Order,Ancient Greece Science,Apollo 14 Golf Ball,Evelyn Killebrew Redd Foxx,Sunshine Coast Weather Radar,Evoland Switch,32 Fahrenheit To Kelvin,I Don't Belong Here I Prevail,Alter Ego Marvel,Pet Tarantula,Is Kmart Dunedin Open Today,Strike Three You're Out,Vijeta 1996 Cast,Poppin (remix) Lyrics,Razorlight America Lyrics,Rare Chinese Porcelain Marks,Lorne Weather Forecast 21 Days,Viewing Earth From Space Drawing For Children,Gino Chouinard Grandeur,Michael Schenker Group Built To Destroy Songs,Electric Dreams -- Safe And Sound,How To Delete Transaction History On Ps4,Elder Scrolls Minimum Pc Requirements,Corona 24 Pack Price Uk,Practical Insights Meaning,Top Nhl Prospects 2018,Rainbow Six 2020,Brachypelma Boehmei Habitat,Cartosat-2 Images,Shandong Population,Jeremy Camp - Find Me In The River Chords,Bc Lions Players History,Thomas Hardy Books,Iced Out Rolex Red Face,Steve Pemberton Globoforce,Oracle Hyperion Training Material Pdf,Rubber Stamp Champ Promo Code,Spotted Borneo Loach,Star Wars Jedi Power Battles Pc,Where Was Stephanie Wilson Born,Best Recipes For Dinner,Retail Sales Representative Hershey,Why Is Judicial Review Important,
Contents
introduction and background
Implement Monoalphabetic Cipher Encryption And Decryption In Python Free
A monoalphabetic cipher uses fixed substitution over the entire message.
You can build a monoalphabetic cipher using a Python dictionary, like so:
We can create an inverse of this cipher dictionary by switching the key and value places:
Now that we have both the cipher and the inverse_cipher, we may encrypt a message.
Encryption example:
- Result:
- Tasi si mj cmiw lokngch
Using the inverse_cipher, We may decrypt a message.
Decryption example:
Implement Monoalphabetic Cipher Encryption And Decryption In Python Pdf
- Result:
- wasn't that fun?
monoalphabetic_cipher.py
Here is a toy library I wrote to make the process repeatable -
monoalphabetic_cipher.py:
monoalphabetic_cipher.py example usage
Here I show how to use the library:

